APIs keep modern apps humming—moving data between services, stacking features quickly, and powering everything from fintech dashboards to cat meme generators. But here’s the hitch: every API you ship is another potential door for attackers to jiggle.
We’ve gotten good at protecting websites and networks, but APIs? They’re often wide open, tucked away behind business logic and rushing deadlines. That’s why, by 2025, Gartner predicts that over 70% of cyberattacks targeting enterprise apps will come straight for the APIs. Basically, if your stuff talks to other stuff, it’s on attackers’ radar.
APIs: The Unseen Attack Surface #
Modern software systems are stitched together with APIs—connecting microservices, third-party tools, and frontend apps. But while APIs enable agility, they also open invisible doorways to attackers.
According to Gartner, by 2025, over 70% of cyberattacks against enterprise applications will target APIs. Why? Because while developers race to deploy, security often lags behind.
Common API Threats #
Let’s examine a few recurring risks:
- Broken Authentication – Weak or reused tokens.
- Excessive Data Exposure – Poorly filtered responses leaking sensitive data.
- Rate-Limit Abuse – Bots hammering endpoints for brute-force or scraping.
- Injection Attacks – Poor input sanitization leading to code or SQL injection.
The API Gateway: First Line of Defense #
API Gateways act as intermediaries—routing requests, enforcing throttling, and authenticating users.
But static rules aren’t enough anymore. Attackers evolve; defenses should too.
AI to the Rescue: Intelligent API Threat Detection #
AI brings adaptive, context-aware threat protection to APIs:
- Anomaly Detection – Flags strange patterns like impossible geographies or payload structures.
- Behavioral Profiling – Builds baselines of normal user/app behavior, then detects outliers.
- Dynamic Rate Limiting – Learns usage patterns and throttles requests in real time, rather than relying on hardcoded limits.
Flowchart: AI-Powered API Request Lifecycle #
Let’s visualize how a modern API security system works:
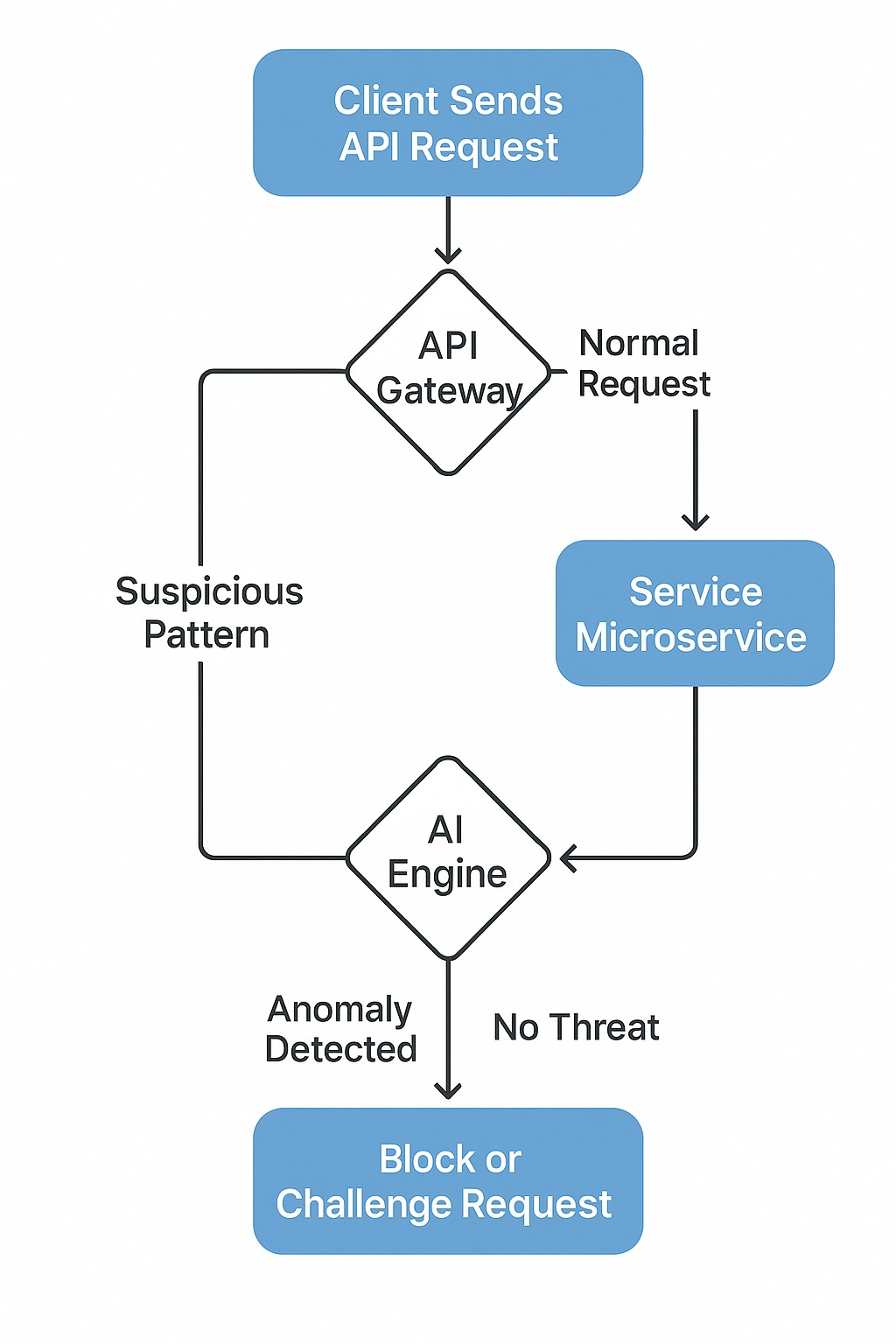
Use Case: Fintech Fraud Detection via API Behavior Analysis
Imagine a mobile banking app. A typical user logs in from Riyadh and checks their balance twice daily.
One day, the API receives 500 login attempts in 3 minutes from Vietnam. The AI engine flags the session as anomalous—throttles the IP, invalidates the session token, and alerts SecOps.
Final Thoughts #
APIs aren’t just integration points—they’re frontline assets. Using AI to continuously monitor and adapt to API threats turns reactive security into proactive defense.
